Do you know which is the first company acquired by Microsoft? Well, the answer is a company called as ‘SOFTIMAGE’ and this acquisition happened on 28 June 1994.
Today, I found the list of official acquisitions by Microsoft here on the website.
http://www.microsoft.com/msft/acquisitions/history.mspx
You may want to have a look at it know more about it. One of my favorite acquisitions is that of Great Plains software in the year 2000 and of course hotmail. Recently, Microsoft has acquired UK based provider of online mapping and location based services called as ‘Multimap’.
Cheers,
Amol
Monday, December 17, 2007
Tuesday, December 04, 2007
Hedging in Finance
Most of us do hedging in our daily lives. Hedging is nothing but securing or should I say insuring yourself from the future loss. For example: when you a buy a house, you also take house insurance. This is in order to prevent loss in future if at all disaster happens. Now, this is again nothing but hedging. In such simple scenarios, you can afford to do hedging by just paying the premium to insurance companies. But in financial markets, hedging is not so simple.
Most of the companies do hedging to avoid loss in the future. They typically rely on derivatives. Options and future are typically used derivative types for hedging by investors. These investors could be single person, corporate companies, banks etc.
The common example of future in Indian market could be hedging done by some big IT companies in India. Due to depreciating US dollar, these companies use future derivatives and so that they get good exchange rate on the future rate. Oil companies, for example, might hedge against the price of oil while an international mutual fund might hedge against fluctuations in foreign exchange rates. An understanding of hedging will help you to comprehend and analyze these investments.
Cheers,
Amol
Most of the companies do hedging to avoid loss in the future. They typically rely on derivatives. Options and future are typically used derivative types for hedging by investors. These investors could be single person, corporate companies, banks etc.
The common example of future in Indian market could be hedging done by some big IT companies in India. Due to depreciating US dollar, these companies use future derivatives and so that they get good exchange rate on the future rate. Oil companies, for example, might hedge against the price of oil while an international mutual fund might hedge against fluctuations in foreign exchange rates. An understanding of hedging will help you to comprehend and analyze these investments.
Cheers,
Amol
Derivatives in Finance
Derivatives are nothing but instruments whose value is derived from the value of something else. In other words, it can be also called as an asset, whose value is derived from other asset. The main types of derivatives are futures, forwards, options, and swaps.
Derivatives are generally used by institutional investors to increase portfolio return or to hedge portfolio risk.
Now, derivatives can be also grouped in 2 different groups such as: over the counter and exchange-traded derivatives. In case of over the counter derivatives, trading happens directly without going through any exchange.
Cheers,
Amol
Derivatives are generally used by institutional investors to increase portfolio return or to hedge portfolio risk.
Now, derivatives can be also grouped in 2 different groups such as: over the counter and exchange-traded derivatives. In case of over the counter derivatives, trading happens directly without going through any exchange.
Cheers,
Amol
Friday, November 30, 2007
Mutual Funds Vs. Hedge Funds
Being an investor, sometimes you may want to know the simple difference between Mutual Funds and Hedge Funds. First of all, both the funds are nothing but managed portfolios. Some one (manager) will pick up the securities that might perform well in future and groups them into a single portfolio. Then investors can actually buy portions of the fund in order to bear losses/gains of that fund.
Now, what does the word hedge mean? We hear this word a lot now days. Terms like hedging, hedge funds have been already part of our vocabularies. For example: most of the big IT companies in India do hedging against the depreciating US $ to increase their profit margins. Basically, hedge means insurance against the bad times or defensive management. Now, the basic differences between mutual fund and hedge funds are:
1. Anybody can invest in mutual funds. The hedge funds are available to only accredited investors. For example: having net worth more that few millions etc. Also, they rarely have more that 500 investors each in hedge fund.
2. Hedge funds are managed more aggressively and the managers can do the short sell of stocks. On this track, mutual funds are more secure.
3. Mutual funds typically adhere to regulations like SEC(in US) and SEBI(in India) for example. The hedge funds are not regulated.
4. Mutual Funds change less fees and also as decided by the regulatory body. Where as hedge funds charge more fees like 1-2% of asset value + percentage of profit etc.
5. Traditional mutual funds generally rely on stock markets to go up but for hedge funds this is not the case. It makes no difference if market goes up or down.
Cheers,
Amol
Now, what does the word hedge mean? We hear this word a lot now days. Terms like hedging, hedge funds have been already part of our vocabularies. For example: most of the big IT companies in India do hedging against the depreciating US $ to increase their profit margins. Basically, hedge means insurance against the bad times or defensive management. Now, the basic differences between mutual fund and hedge funds are:
1. Anybody can invest in mutual funds. The hedge funds are available to only accredited investors. For example: having net worth more that few millions etc. Also, they rarely have more that 500 investors each in hedge fund.
2. Hedge funds are managed more aggressively and the managers can do the short sell of stocks. On this track, mutual funds are more secure.
3. Mutual funds typically adhere to regulations like SEC(in US) and SEBI(in India) for example. The hedge funds are not regulated.
4. Mutual Funds change less fees and also as decided by the regulatory body. Where as hedge funds charge more fees like 1-2% of asset value + percentage of profit etc.
5. Traditional mutual funds generally rely on stock markets to go up but for hedge funds this is not the case. It makes no difference if market goes up or down.
Cheers,
Amol
Tuesday, November 20, 2007
What does it mean to be an Architect?
According to Microsoft Chief Software Architect Ray Ozzie, this is what it means to be an Architect.
"It’s about being exposed to enough tools and techniques of the trade that over time you start to develop a toolkit of different patterns that work in different situations. This is true of software architecture and probably other types of architecture as well. Whether you build bridges or design buildings, you’re trying to apply design patterns to a given situation."
You may want to refer the Architecture Journal.
Cheers,
Amol
"It’s about being exposed to enough tools and techniques of the trade that over time you start to develop a toolkit of different patterns that work in different situations. This is true of software architecture and probably other types of architecture as well. Whether you build bridges or design buildings, you’re trying to apply design patterns to a given situation."
You may want to refer the Architecture Journal.
Cheers,
Amol
VS2008 & .NET 3.5: The wait is over
Microsoft has released Visual Studio 2008 and .NET 3.5 yesterday. With more than 250 new features in VS 2008, it is going to be fun. :):)
Should you want more information on this, you can visit here.
Cheers,
Amol
Should you want more information on this, you can visit here.
Cheers,
Amol
Google Gears
The new buzz word in the web applications market is “Browser extensions”. You may be already aware of Silverlight technology from Microsoft.Now, there is something from Google as well. Google has introduced an open source browser extension called as Google Gears. Though it is still in preliminary stage, developers can use to build future applications.
For .NET developers, the word ‘Smart Client’ is pretty much known. Windows applications can be downloaded using the URL and then run locally using .NET CLR. Users of the application can sync with latest version of the application available on that URL. Now, if you apply this approach broadly to web based application, you will get smart web applications. Isn’t it? These smart web applications will have their own resources to cater user’s needs when offline. This concept has been extended by Google Gears so much that you can actually have web applications running locally now and contacting server on demand basis or when required only.
In order to make your applications Google Gear enabled, user will have to download and install Google Gears from the Google website. Google Gears (or GG) has used AJAX extensively such that now you can have data layer in the client side code. Isn’t it amazing? Developers have been writing web applications since so many years. Now, the time has come for these developers to revisit and re-architect architectures for such applications. Trust me; these designs can be really complex sometimes. Okay, so what is GG all about? Basically, it contains following things:
1. Local server: It caches all the resources like HTML, images, media etc. locally and serves user requests.
2. SQlite database: A data store used for caching the data locally. Then synchronization of this data with the actual server data is big thing.
3. A Worker Thread Pool: It makes application more responsive. Now, one can do so many things in the background using worker thread pool.
One may ask that what Architects have in store for them? Well, first thing is that while architecting offline applications, they need to think about modality of the applications. Then which features should be supported in offline mode and which features in online mode. They also need to think if they really need modal applications or modeless applications. Next big thing is data synchronization. Should this be automatic in the background or manual? Answers to all these questions actually depend on the application’s requirement.
Should you want more information on GG, you can visit this URL.
Cheers,
Amol
For .NET developers, the word ‘Smart Client’ is pretty much known. Windows applications can be downloaded using the URL and then run locally using .NET CLR. Users of the application can sync with latest version of the application available on that URL. Now, if you apply this approach broadly to web based application, you will get smart web applications. Isn’t it? These smart web applications will have their own resources to cater user’s needs when offline. This concept has been extended by Google Gears so much that you can actually have web applications running locally now and contacting server on demand basis or when required only.
In order to make your applications Google Gear enabled, user will have to download and install Google Gears from the Google website. Google Gears (or GG) has used AJAX extensively such that now you can have data layer in the client side code. Isn’t it amazing? Developers have been writing web applications since so many years. Now, the time has come for these developers to revisit and re-architect architectures for such applications. Trust me; these designs can be really complex sometimes. Okay, so what is GG all about? Basically, it contains following things:
1. Local server: It caches all the resources like HTML, images, media etc. locally and serves user requests.
2. SQlite database: A data store used for caching the data locally. Then synchronization of this data with the actual server data is big thing.
3. A Worker Thread Pool: It makes application more responsive. Now, one can do so many things in the background using worker thread pool.
One may ask that what Architects have in store for them? Well, first thing is that while architecting offline applications, they need to think about modality of the applications. Then which features should be supported in offline mode and which features in online mode. They also need to think if they really need modal applications or modeless applications. Next big thing is data synchronization. Should this be automatic in the background or manual? Answers to all these questions actually depend on the application’s requirement.
Should you want more information on GG, you can visit this URL.
Cheers,
Amol
Tuesday, November 06, 2007
Google Android Platform for Mobile Phones
Those of you who have read my previous blog Google Mobile Operating System??
Here is the good news....
"Google on Monday announced a widely expected open-development platform for mobile devices backed by industry heavyweights like T-Mobile, HTC, Qualcomm, and Motorola that could shake the wireless market to its core by simplifying and reducing the cost of developing mobile applications.
The platform, called Android, has been developed by Google and others as part of the Open Handset Alliance, which has over 30 partners supporting it. The goal of this ambitious initiative is to spur innovation in the mobile space and accelerate improvements in how people use the Web via cell phones. "
You may refer to following link for further questions:
Android FAQ
Cheers,
Amol
Here is the good news....
"Google on Monday announced a widely expected open-development platform for mobile devices backed by industry heavyweights like T-Mobile, HTC, Qualcomm, and Motorola that could shake the wireless market to its core by simplifying and reducing the cost of developing mobile applications.
The platform, called Android, has been developed by Google and others as part of the Open Handset Alliance, which has over 30 partners supporting it. The goal of this ambitious initiative is to spur innovation in the mobile space and accelerate improvements in how people use the Web via cell phones. "
You may refer to following link for further questions:
Android FAQ
Cheers,
Amol
Thursday, November 01, 2007
XBRL (eXtensible Business Reporting Language)
XBRL (eXtensible Business Reporting Language) is a language for electronic communication of business and financial data. Again it is one more family of XML and hence it is open source. Typically, in most of the finance reports we treat report as a block on text. What XBRL does is that it gives unique tag/key to each individual data item. What it means is that data item like net profit may have a unique tag in XBRL. Since it is computer readable, computers can read XBRL document, analyze it, parse it and also exchange it with other applications. It increases the comfort factor or ease with which applications can handle financial or business data now.
This introduces one more product line for product based companies. One can write tools/products to transform business data to XBRL format. ;)
Should you want more information on XBRL or XBRL specification, you can visit following URL:
http://www.xbrl.org/SpecRecommendations/
While you are on that site, please do not forget to visit the sample XBRL to resolve all your doubts.
http://www.xbrl.org/Example1/
Cheers,
Amol
This introduces one more product line for product based companies. One can write tools/products to transform business data to XBRL format. ;)
Should you want more information on XBRL or XBRL specification, you can visit following URL:
http://www.xbrl.org/SpecRecommendations/
While you are on that site, please do not forget to visit the sample XBRL to resolve all your doubts.
http://www.xbrl.org/Example1/
Cheers,
Amol
Wednesday, October 24, 2007
Microsoft Silverlight
Over a period of time, web applications/technologies evolved through various phases like CGI, Perl, Java, ASP, ASP.NET, ASP.NET AJAX and now Silverlight. Silverlight is nothing but a web presentation technology which is created to run on separate platforms. So far a great barrier to web applications was user experience. Because of technical constraints, the same user experience of thick client cannot be delivered to web users. It allows us to create rich and interactive experiences which can run on different browsers, different devices and different desktop operating systems as well.
So, what is the foundation of Silverlight technology? The main foundation is XAML i.e. eXtensible Application Markup Language. It is basically XML, which is text-based, providing a firewall-friendly, easy-to-inspect description of the rich contents. Other technologies like Flash, ActiveX or Applets send binary stream to the browser. This is diffcult to audit from security perspective as well as difficult to update. To know more about the architecture of the Silverlight, let us look at the building blocks of it as given below:
• Light-weight browser plug-in:
It has Windows and Macintosh modules designed to enhance Internet Explorer, Firefox and Safari browsers.
• Native Presentation runtime:
Software based browser enhancements allowing rendering of XAML based media in addition to the browser based native rendering of HTML. XAML can be used inline, in a file or in a package.
• Media Pipeline:
Video and audio are handled as media elements in the XAML.
• XAML Parser
Parser is used to parse the XAML before rendering it.
• Programming layer
Silverlight XAML is exposed as DOM model to Javascript. It also supports managed code programming model using the subset of CLR
Should you want more information on this, you can refer to the following URL:
http://silverlight.net/
Cheers,
Amol
So, what is the foundation of Silverlight technology? The main foundation is XAML i.e. eXtensible Application Markup Language. It is basically XML, which is text-based, providing a firewall-friendly, easy-to-inspect description of the rich contents. Other technologies like Flash, ActiveX or Applets send binary stream to the browser. This is diffcult to audit from security perspective as well as difficult to update. To know more about the architecture of the Silverlight, let us look at the building blocks of it as given below:
• Light-weight browser plug-in:
It has Windows and Macintosh modules designed to enhance Internet Explorer, Firefox and Safari browsers.
• Native Presentation runtime:
Software based browser enhancements allowing rendering of XAML based media in addition to the browser based native rendering of HTML. XAML can be used inline, in a file or in a package.
• Media Pipeline:
Video and audio are handled as media elements in the XAML.
• XAML Parser
Parser is used to parse the XAML before rendering it.
• Programming layer
Silverlight XAML is exposed as DOM model to Javascript. It also supports managed code programming model using the subset of CLR
Should you want more information on this, you can refer to the following URL:
http://silverlight.net/
Cheers,
Amol
Tuesday, October 23, 2007
Google mobile operating system??
There have been rumors floating around in the market that Google would come up with the mobile operating system and Google phone as well. Google is now believed to be working on a Linux-based operating system for use on all makes of mobile phone, pitched not against Apple, but rather existing mobile OSs such as Symbian or Microsoft's Windows Mobile.
Whether it will be Google phone or Google mobile operating systems, one thing is clear that Windows mobile developers need to keep an eye on this front too.
Cheers,
Amol
Whether it will be Google phone or Google mobile operating systems, one thing is clear that Windows mobile developers need to keep an eye on this front too.
Cheers,
Amol
Emitting PDFs using Aspose.PDF
Most of the projects have requirements to get reports in Word, Excel, PDF etc. While there are various ways to achieve these objectives, sometimes for quick development it makes sense to use third party component to do the same. I have used one such third party component called as Officewriter from SoftArtisan. And I must say that I was really impressed by this product and its features. It basically emits office documents from the server without actually installing MS office on the server. This is a cool feature for the web based applications. However there is also requirement to generate lot of PDF files these days. I am aware that there are lots of free/open source libraries available on the net to do the same. There are some cool third party components too available. One of them is given below.
Aspose.Pdf is a .Net component for writing Pdf documents without using Adobe Acrobat. It supports converting HTML, Word documents to PDF. It is possible to create PDF using API or XML templates or XSL-FO. The latest version also supports XML Meta data along with form fields, images etc. This component is written in managed code only and till now supports .NET version up to 2.0. If you want have a look at the features available then following is the URL:
http://www.aspose.com/Wiki/default.aspx/Aspose.Pdf/ProductOverview.html
Cheers,
Amol
Aspose.Pdf is a .Net component for writing Pdf documents without using Adobe Acrobat. It supports converting HTML, Word documents to PDF. It is possible to create PDF using API or XML templates or XSL-FO. The latest version also supports XML Meta data along with form fields, images etc. This component is written in managed code only and till now supports .NET version up to 2.0. If you want have a look at the features available then following is the URL:
http://www.aspose.com/Wiki/default.aspx/Aspose.Pdf/ProductOverview.html
Cheers,
Amol
Monday, October 22, 2007
One more sharp language from Microsoft – F#
I have read about F# initiative taken by Microsoft Research lab few years back. I happened to visit the F# initiative again today and hence this blog.
So, what is F#? Is it one more .NET based language with some more cool features? Or is it altogether different programming language?
Well to start with F# is nothing but typed functional programming language for the .NET Framwork. So, next obvious question is what do you mean by functional programming? Well, here is the definition from Wikipedia:
“Functional programming is a programming paradigm that treats computation as the evaluation of mathematical functions and avoids state and mutable data. It emphasizes the application of functions, in contrast with the imperative programming style that emphasizes changes in state”
Most of us may have studied functional programming language in our academics. And that language is called as Lisp. Now, you can relate to the above mentioned definition.
However, F# is not simply a functional language: it is a multi-paradigm language that attempts to capture the best of both functional and object-oriented programming in the context of .NET. Furthermore, even when used as purely functional language F# is remarkable for the sheer power of the libraries and tools available through .NET. F# was designed to be first class citizen on the .NET giving smooth interoperability with other .NET languages. It means that F# can call C#. It also has access to .NET framework APIs, Widnows Presentation Foundation, Windows Communication Foundation, DirectX etc. F# and Ocaml (one more general-purpose programming developed by France National Institute) share a similar core language.
Following are some of the features of the F# language:
•Support for the functional programming features including tuples, lists, options, function values, local function definitions, pattern matching and sequence expressions.
•The powerful type inference mechanisms.
•Support for advanced functional programming constructs such as active patterns and computation expressions.
•F# embraces object-oriented programming and includes support for type-inferred, succinct descriptions of object types.
•Allows types and values in an F# program to be accessed from other .NET languages in a predictable and friendly way.
•Support for a form of meta-programming, inspired by LINQ. This allows data queries to be expressed and type-checked in F# code and then dynamically compiled and translated to target languages such as SQL using the LinqToSql framework.
•Supports .NET generics.
•Supports advanced language and runtime features such as Unicode strings, dynamic linking, preemptive multithreading, and SMP support.
The key application areas for F# on the .NET platform are:
•Mathematically oriented programming
•Scientific and Engineering tasks
•Hardware verification, software verification, optimization, machine learning and compilation etc.
You can find more information on the Microsoft Research home.
Latest update is that Research team is planning to integrate F# with upcoming version of Visual Studio.
So, what it means to programmers? Some one has correctly said, “programmers would chose the best language to write each piece of a coding task, just as a carpenter uses a hammer for one task and a saw for another”.
Cheers,
Amol
So, what is F#? Is it one more .NET based language with some more cool features? Or is it altogether different programming language?
Well to start with F# is nothing but typed functional programming language for the .NET Framwork. So, next obvious question is what do you mean by functional programming? Well, here is the definition from Wikipedia:
“Functional programming is a programming paradigm that treats computation as the evaluation of mathematical functions and avoids state and mutable data. It emphasizes the application of functions, in contrast with the imperative programming style that emphasizes changes in state”
Most of us may have studied functional programming language in our academics. And that language is called as Lisp. Now, you can relate to the above mentioned definition.
However, F# is not simply a functional language: it is a multi-paradigm language that attempts to capture the best of both functional and object-oriented programming in the context of .NET. Furthermore, even when used as purely functional language F# is remarkable for the sheer power of the libraries and tools available through .NET. F# was designed to be first class citizen on the .NET giving smooth interoperability with other .NET languages. It means that F# can call C#. It also has access to .NET framework APIs, Widnows Presentation Foundation, Windows Communication Foundation, DirectX etc. F# and Ocaml (one more general-purpose programming developed by France National Institute) share a similar core language.
Following are some of the features of the F# language:
•Support for the functional programming features including tuples, lists, options, function values, local function definitions, pattern matching and sequence expressions.
•The powerful type inference mechanisms.
•Support for advanced functional programming constructs such as active patterns and computation expressions.
•F# embraces object-oriented programming and includes support for type-inferred, succinct descriptions of object types.
•Allows types and values in an F# program to be accessed from other .NET languages in a predictable and friendly way.
•Support for a form of meta-programming, inspired by LINQ. This allows data queries to be expressed and type-checked in F# code and then dynamically compiled and translated to target languages such as SQL using the LinqToSql framework.
•Supports .NET generics.
•Supports advanced language and runtime features such as Unicode strings, dynamic linking, preemptive multithreading, and SMP support.
The key application areas for F# on the .NET platform are:
•Mathematically oriented programming
•Scientific and Engineering tasks
•Hardware verification, software verification, optimization, machine learning and compilation etc.
You can find more information on the Microsoft Research home.
Latest update is that Research team is planning to integrate F# with upcoming version of Visual Studio.
So, what it means to programmers? Some one has correctly said, “programmers would chose the best language to write each piece of a coding task, just as a carpenter uses a hammer for one task and a saw for another”.
Cheers,
Amol
Thursday, October 18, 2007
Microsoft Vista Service Pack 1
Finally, beta white paper on Widows Vista Service Pack 1 has been released. But the release of RTM would be in the first quarter of 2008. So, what kind of updates will be there in Vista SP1? These updates can be broadly categorized as given below:
1. Quality improvement in terms of security, reliability and performance
2. Improvements to the administration experience including BitLocker Drive Encryption.
3. Support for emerging hardware and standards
In short, SP1 will deliver improvements and enhancements to existing features, but it does not deliver any new OS features as such. For example: It will improve the performance of desktop shell but it does not provide new search user interface.
So, let’s wait patiently until SP1 is released. My guess is that SP1 would come hand in hand with Windows Server 2008 in the next year. MSDN subscribers and partners might get the preview of SP1 later this year.
Cheers,
Amol
1. Quality improvement in terms of security, reliability and performance
2. Improvements to the administration experience including BitLocker Drive Encryption.
3. Support for emerging hardware and standards
In short, SP1 will deliver improvements and enhancements to existing features, but it does not deliver any new OS features as such. For example: It will improve the performance of desktop shell but it does not provide new search user interface.
So, let’s wait patiently until SP1 is released. My guess is that SP1 would come hand in hand with Windows Server 2008 in the next year. MSDN subscribers and partners might get the preview of SP1 later this year.
Cheers,
Amol
Accessing a COM component from the stored procedure
Have you ever thought about accessing a COM component from the SQL Server stored procedure? Well, I have thought about few years back only and since then this is my favorite question while interviewing people.
You may be also aware that .NET CLR can be now also hosted from the SQL Server 2005. Still some times you may require accessing a COM component quickly from the stored procedure especially if you are using SQL Server 2000.
Next question is how to do this? Microsoft SQL Server has lot of system stored procedures. Some of the stored procedures mentioned below can be used to create instance of an OLE component. Once you get the handle, you can also execute exposed methods to get the result. In case of errors, you can also find out the error details.
In short, following are the steps to do this:
• Initialize the DLL from SQL Server using the sp_OACreate method call.
• Call into the various methods or properties of the DLL using sp_OAMethod, sp_OAGetProperty and sp_OASetProperty calls.
• You can get all errors using the sp_OAGetErrorInfo stored procedure.
• Destroy the automation object using sp_OADestroy.
I know what you must be thinking now. Yes, you are right you can create a wrapper over .NET assembly and use it in the stored procedure.
Cheers,
Amol
You may be also aware that .NET CLR can be now also hosted from the SQL Server 2005. Still some times you may require accessing a COM component quickly from the stored procedure especially if you are using SQL Server 2000.
Next question is how to do this? Microsoft SQL Server has lot of system stored procedures. Some of the stored procedures mentioned below can be used to create instance of an OLE component. Once you get the handle, you can also execute exposed methods to get the result. In case of errors, you can also find out the error details.
In short, following are the steps to do this:
• Initialize the DLL from SQL Server using the sp_OACreate method call.
• Call into the various methods or properties of the DLL using sp_OAMethod, sp_OAGetProperty and sp_OASetProperty calls.
• You can get all errors using the sp_OAGetErrorInfo stored procedure.
• Destroy the automation object using sp_OADestroy.
I know what you must be thinking now. Yes, you are right you can create a wrapper over .NET assembly and use it in the stored procedure.
Cheers,
Amol
Banking applications
How does it feel to write applications for a renowned world wide bank? How does if feel when every single line of code is worth of thousand of euros/pounds/ dollars?
Well, I have recently started writing banking applications. The complexity of the domain and the applications sometimes amuses me. The expectations from these applications are tremendous. You have to think about lot of things like: security, performance, user friendliness, scalability, reliability and so on. However it is fun to be part of this.
Cheers,
Amol
Well, I have recently started writing banking applications. The complexity of the domain and the applications sometimes amuses me. The expectations from these applications are tremendous. You have to think about lot of things like: security, performance, user friendliness, scalability, reliability and so on. However it is fun to be part of this.
Cheers,
Amol
24X7 IT support from offshore
Out of the curiosity, I wanted to know what are the activities/phases involved in the maintenance/support project say 24 X 7 projects especially from offshore. Most of the big boys in IT industry serve lot of maintenance contracts. So, it is really good for us to know about that side of IT world. I will mainly focus on the support delivered by the offshore team.
Once RFP is made and customer and IT Company agreed to be in contract, first stage is Due Diligence.
Due Diligence:
In this stage, basically onsite people try to understand the applications which need to be supported. They will have lot of sessions with the customer in order to prepare due diligence documents. It is expected that lot of information is captured in these documents. The information includes lot of things like: technology used for the applications, number of FTEs required, current number of FTEs handling applications, data regarding history tickets raised so far for the applications etc.
Knowledge Transfer:
Once the team is identified, second phase of the contract gets kick started. Knowledge transfer phase typically involve lot of conference calls, live meetings, webex etc. In this phase, customers/SMEs will typically run the offshore team through the applications, application code (depending on what kind tier support is mentioned in the contract like tier-1/2/3/4) End of this phase will make sure that offshore guys are aware of the applications, technologies involved in the contract.
Shadow Support:
Once the Shadow support is started, offshore team solves some percentage of the actual tickets with the help of onsite people and the customer team. Typically, this percentage is between 10-20. The main objective of this phase is to make offshore team aware of the processes and the ways followed to actually solve the tickets with the help of onsite people.
Primary Support:
In this phase, offshore team solves all the tickets without taking much help from the SMEs/customer contact person. Offshore team will come up with the solutions of the tickets and then takes confirmation from the SME to solve it. One important thing to remember here is SME/customer contact person is still available onsite if any help/information/pointers are required by the offshore team to solve the tickets.
Steady State:
This is the final stage, where all the applications mentioned in the contract are completely supported by the offshore team. SMEs need not be required to be present henceforth.
There are so many different models exercised by IT vendors. Some of them will have few people onsite as well to support tier-1 and offshore team will support tier2, 3 and 4. Also, SLAs need to be clearly defined and should be followed strictly. There is whole lot of escalation matrix as well. For project managers, best part would be effort estimations for the support projects. They will have to rely on historical tickets data and in case where historical ticket data is not available then assumptions needs to be done. There are various parameters as well for such assumptions.
I also want to add that I am in the development field only and I have neither switched to support nor I plan to do so in near future. :)
Cheers,
Amol
Once RFP is made and customer and IT Company agreed to be in contract, first stage is Due Diligence.
Due Diligence:
In this stage, basically onsite people try to understand the applications which need to be supported. They will have lot of sessions with the customer in order to prepare due diligence documents. It is expected that lot of information is captured in these documents. The information includes lot of things like: technology used for the applications, number of FTEs required, current number of FTEs handling applications, data regarding history tickets raised so far for the applications etc.
Knowledge Transfer:
Once the team is identified, second phase of the contract gets kick started. Knowledge transfer phase typically involve lot of conference calls, live meetings, webex etc. In this phase, customers/SMEs will typically run the offshore team through the applications, application code (depending on what kind tier support is mentioned in the contract like tier-1/2/3/4) End of this phase will make sure that offshore guys are aware of the applications, technologies involved in the contract.
Shadow Support:
Once the Shadow support is started, offshore team solves some percentage of the actual tickets with the help of onsite people and the customer team. Typically, this percentage is between 10-20. The main objective of this phase is to make offshore team aware of the processes and the ways followed to actually solve the tickets with the help of onsite people.
Primary Support:
In this phase, offshore team solves all the tickets without taking much help from the SMEs/customer contact person. Offshore team will come up with the solutions of the tickets and then takes confirmation from the SME to solve it. One important thing to remember here is SME/customer contact person is still available onsite if any help/information/pointers are required by the offshore team to solve the tickets.
Steady State:
This is the final stage, where all the applications mentioned in the contract are completely supported by the offshore team. SMEs need not be required to be present henceforth.
There are so many different models exercised by IT vendors. Some of them will have few people onsite as well to support tier-1 and offshore team will support tier2, 3 and 4. Also, SLAs need to be clearly defined and should be followed strictly. There is whole lot of escalation matrix as well. For project managers, best part would be effort estimations for the support projects. They will have to rely on historical tickets data and in case where historical ticket data is not available then assumptions needs to be done. There are various parameters as well for such assumptions.
I also want to add that I am in the development field only and I have neither switched to support nor I plan to do so in near future. :)
Cheers,
Amol
Wednesday, August 29, 2007
Leadership vs. Management
Somewhere I read this beautiful line as given below….
“It is often said that if you are in a group of explorers hacking through a thick jungle, the manager is worried about cutting a straight and efficient path, while the leader is climbing the trees to make sure that you are going in the right direction. Fact is that you need both.”
Cheers,
Amol
“It is often said that if you are in a group of explorers hacking through a thick jungle, the manager is worried about cutting a straight and efficient path, while the leader is climbing the trees to make sure that you are going in the right direction. Fact is that you need both.”
Cheers,
Amol
Thursday, July 05, 2007
Google Desktop
I have started to use Google Desktop. This tool has some really cool features to offer. First thing is amazing search capabilities. Just like the web, you can search across your emails, files, music files, videos etc. And it gives you instant results. It does the indexing for all your files on the PC and frees you from having to manually organize your files and emails. Google Desktop also gets integrated with Outlook and you can use it apart from the outlook search feature.
Apart from really powerful search support, it also provides you lot of free gadgets which can be used. Using these gadgets, you can view your mails, listen to music, and check the weather and stock situations. It also provides gadgets for MSN integration and so on. You can use the gadget for Orkut and see Orkut birthday reminders. There are so many gadgets available with Google Desktop. You can explore each one of them if you want.
In short, this is really a cool tool to have on your PC. Also, the sidebar gives you feeling of Longhorn. You can have floating bar if required. You can switch to google online features if required from the desktop. So, what are you waiting for? Just download the tool from the desktop and install on your PC. I am sure that we will see lot of new and awesome features in the Google Desktop in future.
Cheers,
Amol
Apart from really powerful search support, it also provides you lot of free gadgets which can be used. Using these gadgets, you can view your mails, listen to music, and check the weather and stock situations. It also provides gadgets for MSN integration and so on. You can use the gadget for Orkut and see Orkut birthday reminders. There are so many gadgets available with Google Desktop. You can explore each one of them if you want.
In short, this is really a cool tool to have on your PC. Also, the sidebar gives you feeling of Longhorn. You can have floating bar if required. You can switch to google online features if required from the desktop. So, what are you waiting for? Just download the tool from the desktop and install on your PC. I am sure that we will see lot of new and awesome features in the Google Desktop in future.
Cheers,
Amol
Wednesday, May 30, 2007
Navision
Microsoft Business Solutions – Navision
Most of the developers, architects have heard this buzzword as Navision. But apart from knowing that it is kind of accounting/finance related software, other aspects of Navision are not known to people. I have had opportunities to work on Business solutions products/live projects using Dynamics or Navision. Hence I decided to write on Navision first. This blog is just an attempt to introduce Navision to the people who are not aware of its features/ strengths.
Navision is actually Enterprise Resource Management application which provides an efficient way to streamline your business and increase productivity. It is specifically designed to mid-sized companies seeking one solution without disturbing everyday operations. It provides integration functionality support to solutions for: Financial Management, Supply Chain Management, Customer Relationship management and E-Business, Sales Management, Manufacturing and so on. Navision can be installer in 2 different flavors as: 2-tier application or n-tier application.
For 2-tier Navision, DBMS and client reside on different blocks. In case of n-tier application, you have Application server in the middle. Microsoft Navision Application Server acts as a client towards a database server and can act as a server for other services.
Adaptability
The following components deliver adaptability:
o C/SIDE
o Tools for managing C/SIDE
These components make up the core development environment of Navision. They ensure Navision can be customized to support the customer’s unique business now, and as their business changes, grows and encounters new challenges in the future. They help keep the solution problem-free and working as it is expected to do.
Openness
The following technology components deliver openness:
o Navision Application Server
o C/ODBC and C/FRONT
These components help you exchange information in Navision with partners, customers and subsidiaries. They also integrate Navision with other applications and programs.
Efficiency
Two components of Navision help ensure and improve efficiency:
• The client - because it uses the familiar Windows interface, it supports companies who need to work in multiple languages, it offers extensive online help, and you can use hyperlinks for convenient, up-to-the-minute access to relevant data
• User Portal - single-sign-on access to relevant data and services helps streamline operating processes
Reliability
There are 3 technology components to contribute to reliability:
• Navision Database Server
• Microsoft SQL Server Option for Navision
• IBM iSeries Servers for Navision
Together, these components ensure customers can work safely and securely in Navision, without worrying about the reliability of their database. They can be confident Navision will support all employees’ requests, deliver accurate information and make rapid calculations so sums and figures are quickly available.
In so doing, Navision helps your workday run smoothly while supporting your future growth.
Collaboration
Navision takes collaboration to a new level, making it extremely easy for your partners, customers and vendors to do business with you.
It lets you use the Internet and Extensible Markup Language (XML) to exchange and distribute information easily and cost-effectively.
It helps you bring in new partners and customers, while reducing costs internally and helping employees to work more efficiently.
The following 3 technology components deliver collaboration:
• Commerce Gateway
• Commerce Portal
• XBRL
Cheers,
Amol
Most of the developers, architects have heard this buzzword as Navision. But apart from knowing that it is kind of accounting/finance related software, other aspects of Navision are not known to people. I have had opportunities to work on Business solutions products/live projects using Dynamics or Navision. Hence I decided to write on Navision first. This blog is just an attempt to introduce Navision to the people who are not aware of its features/ strengths.
Navision is actually Enterprise Resource Management application which provides an efficient way to streamline your business and increase productivity. It is specifically designed to mid-sized companies seeking one solution without disturbing everyday operations. It provides integration functionality support to solutions for: Financial Management, Supply Chain Management, Customer Relationship management and E-Business, Sales Management, Manufacturing and so on. Navision can be installer in 2 different flavors as: 2-tier application or n-tier application.
For 2-tier Navision, DBMS and client reside on different blocks. In case of n-tier application, you have Application server in the middle. Microsoft Navision Application Server acts as a client towards a database server and can act as a server for other services.
Adaptability
The following components deliver adaptability:
o C/SIDE
o Tools for managing C/SIDE
These components make up the core development environment of Navision. They ensure Navision can be customized to support the customer’s unique business now, and as their business changes, grows and encounters new challenges in the future. They help keep the solution problem-free and working as it is expected to do.
Openness
The following technology components deliver openness:
o Navision Application Server
o C/ODBC and C/FRONT
These components help you exchange information in Navision with partners, customers and subsidiaries. They also integrate Navision with other applications and programs.
Efficiency
Two components of Navision help ensure and improve efficiency:
• The client - because it uses the familiar Windows interface, it supports companies who need to work in multiple languages, it offers extensive online help, and you can use hyperlinks for convenient, up-to-the-minute access to relevant data
• User Portal - single-sign-on access to relevant data and services helps streamline operating processes
Reliability
There are 3 technology components to contribute to reliability:
• Navision Database Server
• Microsoft SQL Server Option for Navision
• IBM iSeries Servers for Navision
Together, these components ensure customers can work safely and securely in Navision, without worrying about the reliability of their database. They can be confident Navision will support all employees’ requests, deliver accurate information and make rapid calculations so sums and figures are quickly available.
In so doing, Navision helps your workday run smoothly while supporting your future growth.
Collaboration
Navision takes collaboration to a new level, making it extremely easy for your partners, customers and vendors to do business with you.
It lets you use the Internet and Extensible Markup Language (XML) to exchange and distribute information easily and cost-effectively.
It helps you bring in new partners and customers, while reducing costs internally and helping employees to work more efficiently.
The following 3 technology components deliver collaboration:
• Commerce Gateway
• Commerce Portal
• XBRL
Cheers,
Amol
Wednesday, May 23, 2007
Design Patterns
Design pattern is typically description of the common problems and approaches to solve those problems. It is most important piece of knowledge to acquire if you are developing applications. Most of the times, we do tend to ignore design. The latest gangs of developers just want to finish off writing code as soon as possible. The existence of classic development IDEs like VS2005, just adds to this. People just write down the application without having a proper look at the application/product vision. Design patterns are typically divided in groups like: creational, structural, behavioral etc. I do not want to stress on these groups. Instead, I will be concentrating on few patterns.
Singleton Pattern: This is the widely popular design pattern. In most of the interviews, interviews will definitely ask you to write down the class using singleton pattern. This pattern makes sure that only one instance of the class is present at any point of time. This is very simple to implement. BUT do make sure that your class is thread-safe. You may want to use mutex or lock in case of C# or synchronized keyword to the method declaration in case of Java.
Factory Method and Factory Type: Factory Method allows a class to defer instantiation to its subclasses. If you are using .NET Framework, then File.Open could be example of the Factory method. Factory type is also called as abstract factory. It allows creation of families of related classes without specifying their concrete classes. Database Factory in .NET 2.0 would be the best example for this. I have used both the patterns liberally whenever I wanted to detach the object creation mechanism from the caller. There are so many classes in .NET which have implemented these patterns themselves.
Façade Pattern: It actually defines high-level interface making subsystem easier to use. Imagine a scenario that one of your team member responsible for business logic layer, has left. Later you realize that to execute one functionality, you have to call 4 different functions and instantiate 3 different classes. Your UI guys will not like this obviously. You may think of using façade pattern here and simplifying things for UI developers. Trust me they will pray for you. ;)
Adapter Pattern: This pattern is typically used to remove the incompatibility issues between different classes. It typically converts one interface into the interface that is expected by the other class. I like one example which I have read from one of the books on design patterns. Consider that you have been to use new Framework B for communication with Framework C. You already have Framework A for talking to Framework B. And now your CEO told you to use Framework B as well because it is developed by his nephew. This is the situation where you can use adapter pattern. How? I will left it to the readers. ;)
Flyweight pattern: This pattern mainly focuses on reusability. Instead of having large objects, you can use a set of common objects called as Flyweights. You can take the common functionalities in put in these flyweight objects. It is mainly used for efficient sharing.
Apart from these there are other popular patterns like: observer, mediator, chain of responsibility, proxy pattern etc.
It is good to know these patterns. So, next time when you design something or write code, you know what patterns to use.
Cheers,
Amol
Singleton Pattern: This is the widely popular design pattern. In most of the interviews, interviews will definitely ask you to write down the class using singleton pattern. This pattern makes sure that only one instance of the class is present at any point of time. This is very simple to implement. BUT do make sure that your class is thread-safe. You may want to use mutex or lock in case of C# or synchronized keyword to the method declaration in case of Java.
Factory Method and Factory Type: Factory Method allows a class to defer instantiation to its subclasses. If you are using .NET Framework, then File.Open could be example of the Factory method. Factory type is also called as abstract factory. It allows creation of families of related classes without specifying their concrete classes. Database Factory in .NET 2.0 would be the best example for this. I have used both the patterns liberally whenever I wanted to detach the object creation mechanism from the caller. There are so many classes in .NET which have implemented these patterns themselves.
Façade Pattern: It actually defines high-level interface making subsystem easier to use. Imagine a scenario that one of your team member responsible for business logic layer, has left. Later you realize that to execute one functionality, you have to call 4 different functions and instantiate 3 different classes. Your UI guys will not like this obviously. You may think of using façade pattern here and simplifying things for UI developers. Trust me they will pray for you. ;)
Adapter Pattern: This pattern is typically used to remove the incompatibility issues between different classes. It typically converts one interface into the interface that is expected by the other class. I like one example which I have read from one of the books on design patterns. Consider that you have been to use new Framework B for communication with Framework C. You already have Framework A for talking to Framework B. And now your CEO told you to use Framework B as well because it is developed by his nephew. This is the situation where you can use adapter pattern. How? I will left it to the readers. ;)
Flyweight pattern: This pattern mainly focuses on reusability. Instead of having large objects, you can use a set of common objects called as Flyweights. You can take the common functionalities in put in these flyweight objects. It is mainly used for efficient sharing.
Apart from these there are other popular patterns like: observer, mediator, chain of responsibility, proxy pattern etc.
It is good to know these patterns. So, next time when you design something or write code, you know what patterns to use.
Cheers,
Amol
Monday, February 19, 2007
Windows CardSpace
Hello,
Each one of us has different identities in this real world. When you talk to your parents, you are using identity of son or daughter. When you communicate with your children, your identity is of father or mother. When you are in office, you are the boss. When you just hang around with your friend, you immediately wear friend’s hat. Thus we have different identities in our daily lives. Similarly, your driving license, passport, credit card, bank passbook, telephone bill, ration card, social security number etc. represent your different identities.
If we have so many identities in the physical world, then think about virtual world. Every day you access so many sites entering site specific user name and password or using your credit card number to buy airline tickets or your user name for e-mail account etc. Every single application provider has his own security mechanism. Good thing is that there are some common mechanisms as well like: https, Kerberos etc. Okay, so how do we deal with these DIGITAL IDENTITIES in this world of internet? Let us look at the some typical examples as curtain raiser for CardSpace. Then we will dive somewhat deep in the Windows CardSpace.
“Think about what happens, for instance, when you access an online airline tickets booking application such as Air India. In the simplest case, no digital identity is involved—anybody can browse through the tickets, without telling who they are. When you try to place an order, however, you need to log in, which requires providing a digital identity. Today, you'll most likely do this by entering a username and password, both of which you've chosen yourself. If this online booking application also supports CardSpace, it will provide another option for identifying yourself: using an information card. To allow this, the airline might have a separate button on its login screen that you can click to log in with an information card, rather than entering your username and password.
Clicking this button causes the browser to use CardSpace to log in to this site. As usual, you'll be presented with the CardSpace selection screen, and you'll choose one of the cards in order to identify yourself. Since all the site needs to do at this point is identify you as a unique customer, this simple form of digital identity is sufficient. To pay for your purchases, you might enter your credit card information and mailing address on a Web form as usual.
In this simple scenario, CardSpace provided a way to log in to an online booking without using a password. This is useful, and it's a step forward for digital identity on the Internet.”
I know this example will not be sufficient enough to know what exactly CardSpace is but it will definitely give some massage to your brain so that your neurons start moving in the right direction.
Despite having different digital identities, one this is sure that when information is transferred using any protocol, it is represented in some kind of security tokens. I would say security token is just collections of claims. Let us not dive deep within security tokens. But what will happen if you have only one digital identity that can be used across the applications? Life will be good in that case but unfortunately that is not so easy to implement for the obvious reasons. So, the real challenge is to manage different identities instead of having one identity for all purpose. Yes, now you are coming close to Windows CardSpace.
It uses Identity metasystem which is like system of systems. The identity metasystem provides a consistent way to work with multiple digital identities, regardless of the kinds of security tokens they use. Using standard protocols that anyone can implement on any platform, the identity metasystem allows the acquisition and use of any kind of security tokens to convey identity. So, now what is CardSpace?
Here is the definition, direct from the God: “Windows CardSpace (formerly "InfoCard") is a Microsoft .NET Framework version 3.0 (formerly WinFX) component that provides the consistent user experience required by the identity metasystem. It is specifically hardened against tampering and spoofing to protect the end user's digital identities and maintain end-user control.”
Main aspects of the CardSpace are as given below:
1. Support for diverse digital identities
2. Empowering users to make good decisions about using their digital identities.
3. Replacement of password-based Web login
4. Improving user confidence in using such identities, making application secure. MS is also working on higher-assurance certificates apart from using server side certificates using SSL etc.
Now, how does it really work? Are there any user roles defined? Yes, there are three mail roles defined as given below:
1. User
2. Identity Provider
3. Relying Parties
User is the entity associated with digital identity. Where as Identity Provider provides digital identity to the user. And Relying Parties are those (applications) who accept digital identities and then decide to authenticate or authorize etc.
Following is the diagram for the same depicting how it works.
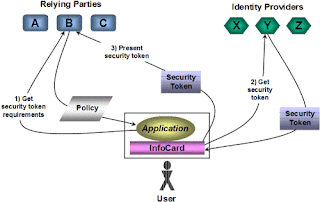
FAQ:
http://windowshelp.microsoft.com/Windows/en-US/Help/7dc9c520-9d16-473d-b21b-413ac7226fb61033.mspx
Thanks and Best Regards,
Amol Kulkarni
Each one of us has different identities in this real world. When you talk to your parents, you are using identity of son or daughter. When you communicate with your children, your identity is of father or mother. When you are in office, you are the boss. When you just hang around with your friend, you immediately wear friend’s hat. Thus we have different identities in our daily lives. Similarly, your driving license, passport, credit card, bank passbook, telephone bill, ration card, social security number etc. represent your different identities.
If we have so many identities in the physical world, then think about virtual world. Every day you access so many sites entering site specific user name and password or using your credit card number to buy airline tickets or your user name for e-mail account etc. Every single application provider has his own security mechanism. Good thing is that there are some common mechanisms as well like: https, Kerberos etc. Okay, so how do we deal with these DIGITAL IDENTITIES in this world of internet? Let us look at the some typical examples as curtain raiser for CardSpace. Then we will dive somewhat deep in the Windows CardSpace.
“Think about what happens, for instance, when you access an online airline tickets booking application such as Air India. In the simplest case, no digital identity is involved—anybody can browse through the tickets, without telling who they are. When you try to place an order, however, you need to log in, which requires providing a digital identity. Today, you'll most likely do this by entering a username and password, both of which you've chosen yourself. If this online booking application also supports CardSpace, it will provide another option for identifying yourself: using an information card. To allow this, the airline might have a separate button on its login screen that you can click to log in with an information card, rather than entering your username and password.
Clicking this button causes the browser to use CardSpace to log in to this site. As usual, you'll be presented with the CardSpace selection screen, and you'll choose one of the cards in order to identify yourself. Since all the site needs to do at this point is identify you as a unique customer, this simple form of digital identity is sufficient. To pay for your purchases, you might enter your credit card information and mailing address on a Web form as usual.
In this simple scenario, CardSpace provided a way to log in to an online booking without using a password. This is useful, and it's a step forward for digital identity on the Internet.”
I know this example will not be sufficient enough to know what exactly CardSpace is but it will definitely give some massage to your brain so that your neurons start moving in the right direction.
Despite having different digital identities, one this is sure that when information is transferred using any protocol, it is represented in some kind of security tokens. I would say security token is just collections of claims. Let us not dive deep within security tokens. But what will happen if you have only one digital identity that can be used across the applications? Life will be good in that case but unfortunately that is not so easy to implement for the obvious reasons. So, the real challenge is to manage different identities instead of having one identity for all purpose. Yes, now you are coming close to Windows CardSpace.
It uses Identity metasystem which is like system of systems. The identity metasystem provides a consistent way to work with multiple digital identities, regardless of the kinds of security tokens they use. Using standard protocols that anyone can implement on any platform, the identity metasystem allows the acquisition and use of any kind of security tokens to convey identity. So, now what is CardSpace?
Here is the definition, direct from the God: “Windows CardSpace (formerly "InfoCard") is a Microsoft .NET Framework version 3.0 (formerly WinFX) component that provides the consistent user experience required by the identity metasystem. It is specifically hardened against tampering and spoofing to protect the end user's digital identities and maintain end-user control.”
Main aspects of the CardSpace are as given below:
1. Support for diverse digital identities
2. Empowering users to make good decisions about using their digital identities.
3. Replacement of password-based Web login
4. Improving user confidence in using such identities, making application secure. MS is also working on higher-assurance certificates apart from using server side certificates using SSL etc.
Now, how does it really work? Are there any user roles defined? Yes, there are three mail roles defined as given below:
1. User
2. Identity Provider
3. Relying Parties
User is the entity associated with digital identity. Where as Identity Provider provides digital identity to the user. And Relying Parties are those (applications) who accept digital identities and then decide to authenticate or authorize etc.
Following is the diagram for the same depicting how it works.

FAQ:
http://windowshelp.microsoft.com/Windows/en-US/Help/7dc9c520-9d16-473d-b21b-413ac7226fb61033.mspx
Thanks and Best Regards,
Amol Kulkarni
Subscribe to:
Posts (Atom)